Many web applications that you can find on the Internet today may have vulnerabilities and attack strategies that can be exploited by some attacker that wants the administrator role in your server or just want to access sensitive data on it. Using Nmap and the http-enum.nse script you can get an overview of those applications, directories and files exposed. In this way you check for vulnerabilities in databases for or exploits. Through this method, you can find serious (and very stupid) security flaws on your website like the availability of folders that should be deleted once the project has been finalized e.g WordPress, PrestaShop etc. and thereby, you can find a solution for it.
What is Nmap?
Nmap (Network Mapper) is a free and open source (license) utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts.
In this article we are going to enumerate the directories of a webserver with it.
1. Download http-enum.nse file
A NSE file (Nmap Scripting Engine) is one of Nmap's most powerful and flexible features. It allows users to write (and share) simple scripts (using the Lua programming language ) to automate a wide variety of networking tasks. Those scripts are executed in parallel with the speed and efficiency you expect from Nmap. Users can rely on the growing and diverse set of scripts distributed with Nmap, or write their own to meet custom needs.
In this case we are going to need the http-enum.nse script available in the official website. You can download http-enum.nse from this link. For more information visit the http-enum website of nmap here. Be sure to download the file in your computer with the respective extension (.nse) and proceed with the step 2 (in this case our .nse script will be located in /root/hacking/).
2. Gathering directories information with Nmap
To gather information about the directories of a web server with nmap, you can use the following command:
nmap -v --script [path to http-enum.nse file] [web domain or IP]See the following examples to see how you can execute the command with the replaced values:
nmap -v --script /root/hacking/http-enum.nse yourdomain.com
# Or with the IP
nmap -v --script /root/hacking/http-enum.nse 127.0.0.1The output in your terminal will be something like:
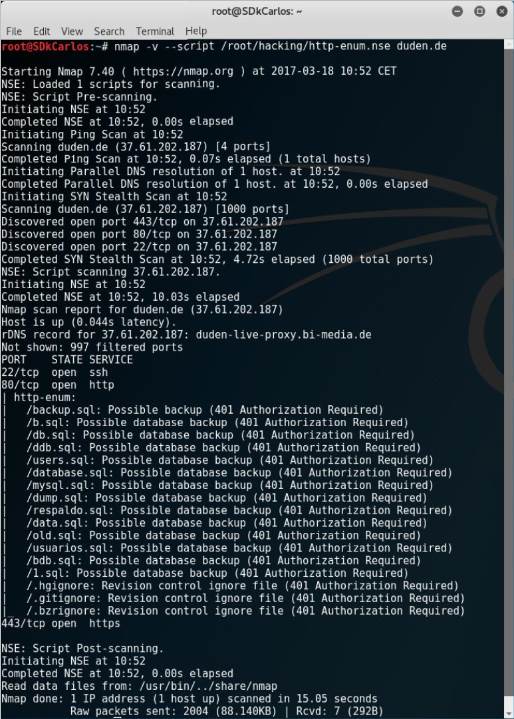
Happy security review !








