"Why can't I connect to the network even though my computer got its IP address on its own?" Have you face these kinds of problems in your everyday life? Have you ever disbelieved whether or not the IP address was real? Whether it came from a valid DHCP server? If not, how can you stop this? In this post, we'll talk about a term called "DHCP Snooping" to help users stay away from illegal IP addresses.
Check out the detailed blog about Dynamic ARP inspection & DHCP Snooping.
What Is DHCP Snooping?
DHCP Snooping is a layer 2 security technology built into the operating system of a network switch that drops DHCP traffic that is deemed unacceptable. DHCP Snooping stops rogue DHCP servers from giving IP addresses to DHCP clients without permission. The following things are done by the DHCP Snooping feature:
Validates DHCP messages from sources that can't be trusted and filters out messages that aren't valid.
Builds and manages the DHCP Snooping binding database, which has information about untrusted hosts with leased IP addresses.
Uses the DHCP Snooping binding database to verify requests from hosts that are not trusted.
DHCP Snooping: How Does It Work?
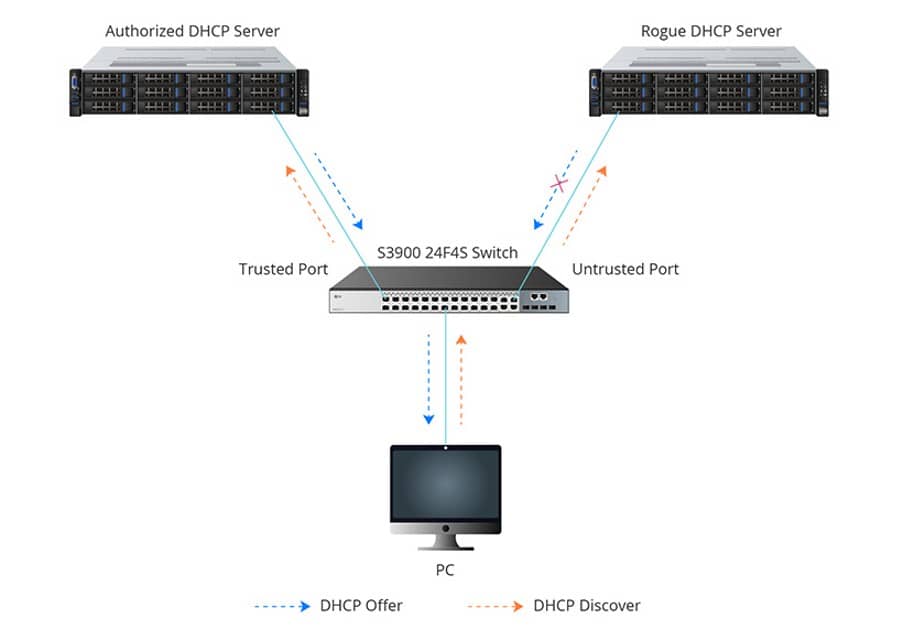
Figure 2 shows that DHCP Snooping divides interfaces on the switch into two groups: trusted ports and untrusted ports. A trusted port is a port or source whose messages from the DHCP server can be trusted. A port from which DHCP server messages are not trusted is called a "untrusted port." DHCP offer messages can only be sent through the trusted port if DHCP Snooping is turned on. If not, it will be thrown out.
In the acknowledgment stage, a DHCP binding table is made based on the DHCP ACK message. Figure 3 shows that it writes down the host's MAC address, the leased IP address, the lease time, the binding type, and the VLAN number and interface information. If the next DHCP packet from a host that can't be trusted doesn't match the information, it will be thrown away.
DHCP Snooping Can Stop Common Attacks
Attack on DHCP Spoofing
When an attacker responds to DHCP requests by trying to list himself as the default gateway or DNS server, this is called DHCP spoofing. This starts a "man in the middle" attack. With that, they might be able to intercept user traffic before it gets sent to the real gateway or cause a denial of service (DoS) by flooding the real DHCP server with requests to use up all the available IP addresses.
DHCP Starvation Attack
Network DHCP servers are often the target of DHCP starvation attacks, which try to flood the authorised DHCP server with DHCP REQUEST messages with fake source MAC addresses. Since the DHCP server doesn't know that this is a DHCP starvation attack, it will respond to all requests by giving out available IP addresses. This will cause the DHCP pool to run out of IP addresses.
How do you turn on DHCP snooping?
Only wired users can use DHCP Snooping. As a security feature for the access layer, it is mostly turned on on any switch with access ports in a VLAN that is serviced by DHCP. Before you turn on DHCP Snooping on the VLAN you want to protect, you need to set up the trusted ports. These are the ports through which real DHCP server messages will flow. Both the CLI interface and the Web GUI can be used to do this.
Read also: How to enumerate for privilege escalation on a Linux target with LinPEAS
Conclusion
Even though DHCP makes IP addressing easier, it also makes security worries more likely. To deal with the problems, one of the security measures, DHCP Snooping, can stop the rogue DHCP server from giving out invalid DHCP addresses and can stop an attack that tries to use up all the DHCP addresses. The gigabit stackable managed switches in the FS S3900 series can make the most of this feature to protect your network.






