On January 3rd, 2018, the Project Zero team at Google announced the "discovery" of the Meltdown and Spectre exploits targeting processors created by Intel, AMD and ARM, which use the “CPU data cache timing” to “leak information out of mis-speculated execution”, with the afirmation that "Nearly Every Computer Made Since 1995 Is Dangerously Flawed." Meltdown and Spectre are security vulnerabilities in 64-bit Intel central processing units (CPUs) which grant access to privileged system memory to unauthorized processes and allows cyber attacks to trick error-free programs into leaking sensitive data.
Although as mentioned the issue goes back to 1995, it's only coming out till the date, however the history behind this is complex and we won't discuss it here. One thing is sure, a lot of server admins panicked once they saw this controversy in the digital newspaper and immediately searched for a solution. However, before applying a solution you may want to know if you are vulnerable to the issue right? The most common answer will be "certainly, yes". However, just to (waste some time on your job) be sure, you may confirm this issue by yourself with the help of the spectre-meltdown-checker shell script.
In this article, we'll show you how to detect if your server processor is vulnerable to Meltdown and Spectre with the help of an open source shell script.
1. Download spectre-meltdown-checker.sh
Spectre-meltdown-checker is a very simple shell script that tells if your Linux/Ubuntu installation is vulnerable against the 3 "speculative execution" CVEs that were made public early 2018. Without options, it'll inspect your currently running kernel. You can also specify a kernel image on the command line, if you'd like to inspect a kernel you're not running. The script will do its best to detect mitigations, including backported non-vanilla patches, regardless of the advertised kernel version number.
Disclaimer
The spectre-meltdown-checker script has a very clear disclaimer that you should read before using it in your server:
This tool does its best to determine whether your system is immune (or has proper mitigations in place) for the
collectively named "speculative execution" vulnerabilities. It doesn't attempt to run any kind of exploit, and can't guarantee
that your system is secure, but rather helps you verifying whether your system has the known correct mitigations in place.
However, some mitigations could also exist in your kernel that this script doesn't know (yet) how to detect, or it might
falsely detect mitigations that in the end don't work as expected (for example, on backported or modified kernels).
Your system exposure also depends on your CPU. As of now, AMD and ARM processors are marked as immune to some or all of these
vulnerabilities (except some specific ARM models). All Intel processors manufactured since circa 1995 are thought to be vulnerable.
Whatever processor one uses, one might seek more information from the manufacturer of that processor and/or of the device
in which it runs.
The nature of the discovered vulnerabilities being quite new, the landscape of vulnerable processors can be expected
to change over time, which is why this script makes the assumption that all CPUs are vulnerable, except if the manufacturer
explicitly stated otherwise in a verifiable public announcement.
This tool has been released in the hope that it'll be useful, but don't use it to jump to conclusions about your security.
If you agree with the disclaimer, then let's get started ! Obviously to run the script you will need its source, you can download the sh file from the repository or you can download it using wget:
wget https://raw.githubusercontent.com/speed47/spectre-meltdown-checker/master/spectre-meltdown-checker.shOr if you prefer to use Curl:
curl https://raw.githubusercontent.com/speed47/spectre-meltdown-checker/master/spectre-meltdown-checker.sh --output spectre-meltdown-checker.shYou can save the script wherever you want as long as you can access the directory later. For more information about this useful script, please visit the official repository at Github.
2. Give execution permission to the file
As next, as the script is from a third party source it won't have the right permissions, specifically adding the executable permissions with chmod:
Note
You can skip this step if you can execute the file using sudo bash ./spectre-meltdown-checker.sh in the third step.
chmod +x ./spectre-meltdown-checker.shNow the file should be executable from the terminal.
3. Run the script
According to the permissions that you have for the file, you may be able to execute it using the following command (if you used chmod +x):
sudo ./spectre-meltdown-checker.shOtherwise without adding permissions to the file, just run the script using sudo bash:
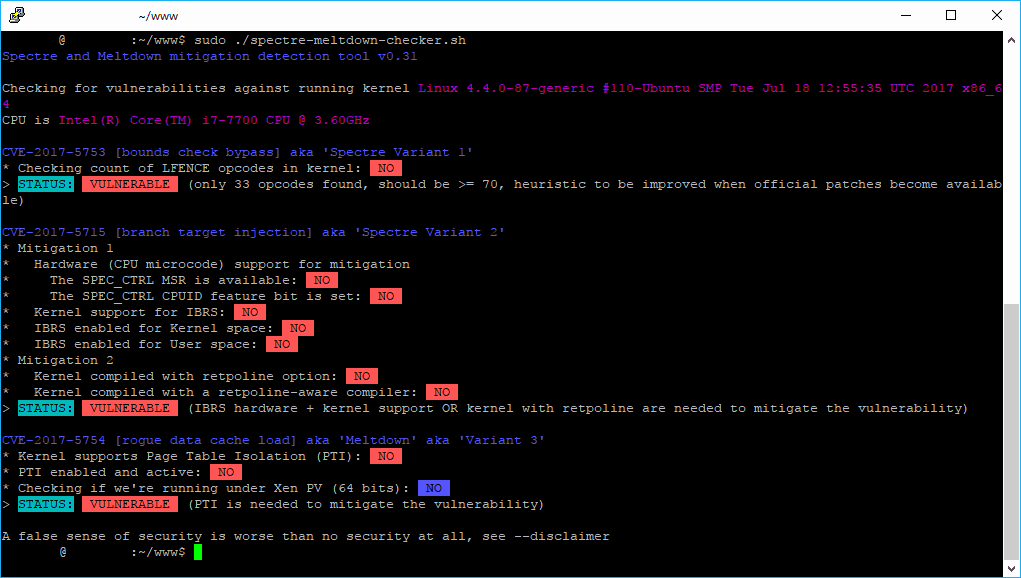
sudo bash ./spectre-meltdown-checker.shThis will start the tool and in matter of seconds you will know if your processor is vulnerable to Spectre or Meltdown:
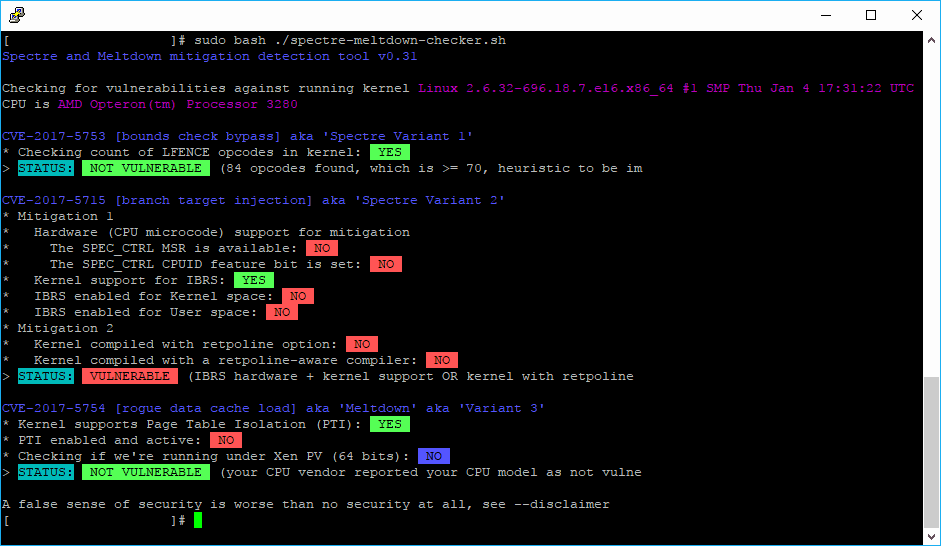
Both exploits are aimed at the “kernel,” an essentially invisible part of your device’s operating system that is perhaps the most vital software component on your computer (or phone or tablet). It’s the go-between for all of your applications and basic parts of your computer: the processor, the memory, and the device itself (think your keyboard and touchpad on a laptop, or the power button on your phone). Having said that, although this article doesn't target how to solve the issue but how to detect it, short said, your problem could be solved by updating the kernel of your server. Digital Ocean published an useful article about how to fix these flaws, which basically consists of updating your system software, mainly the Kernel (yum, apt-get, dnf).
For more information about Spectre and Meltdown, be sure to check the Google Zero blog article or the Spectre Attack website here.
Happy security review !