Network segmentation is a core component of implementing cybersecurity “defense in depth”. Rather than protecting only the network perimeter – and leaving the organization vulnerable to attackers that breach this boundary – network segmentation creates multiple boundaries within the company network, increasing the probability that an attacker will be detected and blocked before they achieve their objective or significant damage is done.
Segmenting traditional, on-premises networks is relatively simple since the organization controls their own network infrastructure. However, most corporate networks are no longer contained within the traditional network perimeter.
Segmenting the modern, global WAN requires a new approach to security. Software-defined wide area networking (SD-WAN) provides a potential solution. An understanding of SD-WAN benefits and how they relate to network segmentation can help in making the right choice of a network segmentation solution.
The Importance of Internal Network Segmentation
In the past, most organizations relied upon a perimeter-focused network security model. This involves deploying a stack of security solutions at the network perimeter that will inspect all traffic entering and leaving the network. As long as all cyber threats originate from outside of the network and the organization’s security deployment can perfectly detect and block incoming threats, then this is a workable security model.
However, neither of these assumptions is valid. A growing percentage of data breaches are caused or enabled by internal actors, whether intentionally or otherwise. And the number of successful cyberattacks against business that occur on a daily basis demonstrates that no cybersecurity infrastructure is perfect.
Internal segmentation is designed to decrease cyber risk by breaking the enterprise network into a number of independent zones. The perimeter of each zone is then protected by a network firewall and, potentially, other cybersecurity solutions, providing it with a similar level of protection as the network perimeter.
This internal segmentation is valuable for cybersecurity since it reduces the risk and impact associated with a successful cyberattack. Once an attacker gains access to an organization's network, it is likely that they will need to pass through additional internal segmentation boundaries to achieve their objective. Each of these provides an organization with an additional opportunity to identify and respond to an attacker before any damage is done.
Modern Networks Are Not On-Premises
Network segmentation for traditional on-premises networks is relatively simple. Most organizations have complete control over their internal network infrastructure, including everything from the routers to the network cables. This enables them to implement internal segmentation either physically or logically, via virtual LANs (VLANS), by routing traffic that crosses segment boundaries through internal firewalls.
However, the traditional on-premises network is becoming rarer and rarer. Most organizations have enthusiastically embraced cloud computing, moving storage and processing of critical data off-premises to the infrastructure provided by their cloud service provider (CSP). This – in combination with a growth of telework and the expansion of organizations to include multiple physical sites – means that business traffic now commonly flows over the public Internet, which the organization does not control, in order to reach its intended destination.
As networks grow and evolve, traditional approaches to network segmentation are rapidly becoming obsolete. Deploying physical firewalls on the corporate LAN and routing all traffic through it to enforce segmentation boundaries is no longer feasible. As telecommuting becomes more popular and critical processes move to Software as a Service (SaaS) infrastructure, business traffic increasingly begins and terminates outside of the corporate network boundary. Forcing this traffic to flow through the enterprise LAN for inspection and policy enforcement creates unacceptable levels of latency and places additional load on already strained perimeter-based cybersecurity infrastructure.
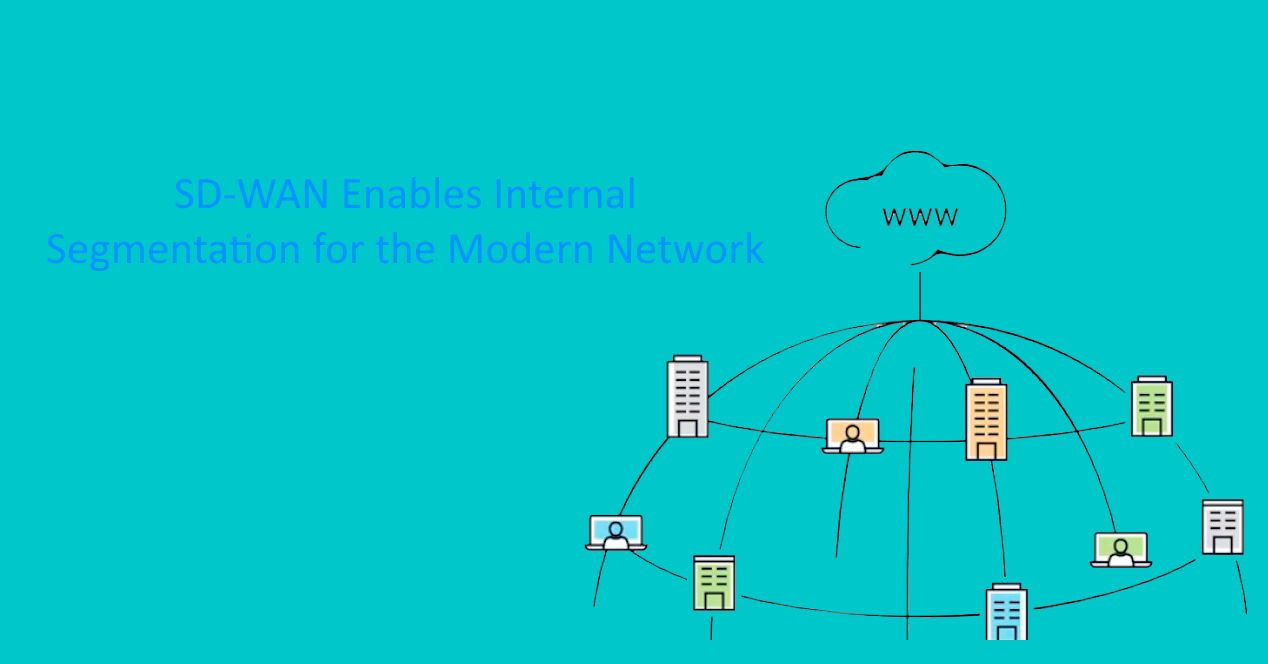
SD-WAN Segments the Corporate WAN
As enterprise networks expand and evolve, the need for internal segmentation grows as well. If an enterprise cannot fully trust the endpoints connected to the corporate WAN, segmentation is a necessary tool for limiting risk and the potential impacts of an insider threat. However, implementing network segmentation for the corporate WAN requires a modern approach to segmentation.
Secure SD-WAN is a network security technology designed for the modern WAN. It enables organizations to move security functionality to the network edge by consolidating networking and security functionality within a single appliance.
SD-WAN enables an organization to implement “internal” network segmentation on their WAN without forcing all traffic to flow through the headquarters location. By scattering SD-WAN appliances through the corporate WAN, traffic can be routed via the nearest SD-WAN solution for security scanning and policy enforcement before continuing on to its destination. This limits the impact of security on network performance.
From SD-WAN to SASE
The benefits of SD-WAN are limited by the number of locations where an organization can deploy it. This is why Secure Access Service Edge (SASE) is commonly considered the future of network security.
By taking the functionality of a secure SD-WAN appliance and moving it to the cloud, SASE enables an organization to strategically deploy security infrastructure near common traffic sources and destinations. This allows implementation of network segmentation using SD-WAN with minimal infrastructure investment and impact on network performance.