FTPS (File Transfer Protocol with support for Transport Layer Security (SSL/TLS)), FTP (File Transfer Protocol) and SFTP (SSH File Transfer Protocol) are basically protocols that grants remote file transfer capabilities between a client and a server.
But, what are they and what is the difference between them? Learn what are and what's the difference between 3 of the most notorious (and similar name) transfer protocols.
FTP
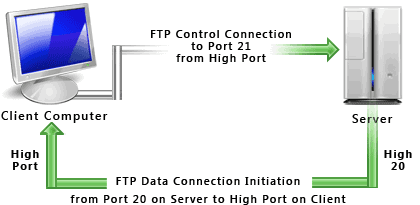
FTP is used to transfer files between computers on a network. You can use FTP to exchange files between computer accounts, transfer files between an account and a desktop computer, or access online software archives. Keep in mind, however, that many FTP sites are heavily used and require several attempts before connecting.
Using FTP both the command and data channels are unencrypted. Any data sent over these channels can be intercepted and read. One common exploit that takes advantage of this particular vulnerability is the man-in-the-middle attack using ARP poisoning and a packet sniffer.
Pros.
- Allows you to transfer multiple files as well as directories.
- The ability to resume a transfer if the connection is lost.
- The ability to add items to a “queue” to be uploaded/downloaded.
- Many FTP clients have the ability to schedule transfers.
- No size limitation on single transfers (browsers only allow up to 2 GB).
- Many clients have scripting capabilities through command line.
- Most clients have a synchronizing utility.
- Faster transfers then HTTP.
Cons.
- Usernames, passwords and files are sent in clear text.
- Filtering active FTP connections is difficult on your local machine (passive is preferred).
- Servers can be spoofed to send data to a random port on an unintended computer.
- Hard to script jobs.
- TLS 1.2 not always supported over https (use cURL instead) (per Steve Silberberg atFitpacking).
- Easy for inexperienced users to wipe out work (per Sam Williamson at WeSwap Travel Money).
- Inconsistency/inability to track what has been uploaded on the remote system (per John Chapin at Capital Technology Services).
FTPS
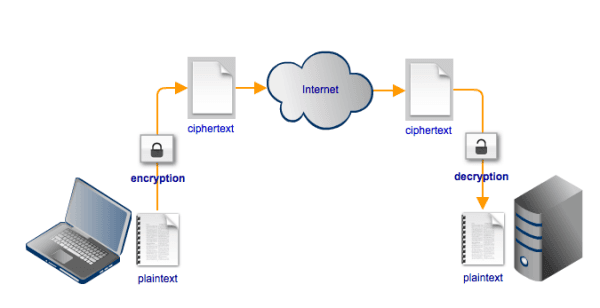
FTPS (FTP/SSL) is a name used to provide a number of ways that FTP software can perform secure file transfers. Each way involves the use of a SSL/TLS layer below the standard FTP protocol to encrypt the control and/or data channels.
When the FTP protocol was initially drafted security was not a concern. Since then many things have changed and sending data over any public network without encryption is considered very risky and in some cases prohibited. Regulations like PCI-DSS and HIPAA, for instance, contain provisions that require data transmissions to be protected by encryption. In order to solve this issue comes out the extension to the original FTP (RFC 2228) that protect FTP data as it travels over the network using SSL encryption.

Pros.
- Widely known and used.
- The communication can be read and understood by a human.
- Provides services for server-to-server file transfer.
- SSL/TLS has good authentication mechanisms (X.509 certificate features).
- FTP and SSL/TLS support is built into many internet communications frameworks.
Cons.
- Does not have a uniform directory listing format.
- Requires a secondary DATA channel, which makes it hard to use behind firewalls.
- Does not define a standard for file name character sets (encodings).
- Not all FTP servers support SSL/TLS.
- Does not have a standard way to get and change file or directory attributes.
SFTP
SFTP (SSH File Transfer Protocol) is a network protocol that provides file transfer and manipulation functionality over any reliable data stream. SFTP service is typically used with the SSH-2 protocol (TCP port 22) to provide secure file transfer, but is intended to be usable with other protocols as well.
SFTP abbreviation is often mistakenly used to specify some kind of Secure FTP, by which people most often mean FTPS. Another (similar) mistake is that SFTP is thought to be some kind of FTP over SSL. In fact SFTP is an abbreviation of SSH File Transfer Protocol. This is not FTP over SSL and not FTP over SSH (which is also technically possible, but very rare).
Pros:
- Has good standards background which strictly defines most (if not all) aspects of operations.
- Has only one connection (no need for DATA connection).
- The connection is always secured.
- The directory listing is uniform and machine-readable.
- The protocol includes operations for permission and attribute manipulation, file locking and more functionality.
Cons:
- The communication is binary and can’t be logged "as is" for human reading.
- SSH keys are harder to manage and validate.
- The standards define certain things as optional or recommended, which leads to certain compatibility problems between different software titles from different vendors.
- No server-to-server copy and recursive directory removal operations.
- No built-in SSH/SFTP support in VCL and .NET frameworks.
Differences
|
|
FTP |
FTPS |
SFTP |
|
Security |
Unencrypted information exchange in both command and data channels. Communication is human readable. |
Encryptions happens on both command and data channels via either implicit SSL or explicit SSL. Communication is human-readable. |
All information exchange between the FTP server and client are encrypted via SSH protocol. SFTP can also encrypts the session. Communication is not human-readable as it’s in a binary format. |
|
Firewall Port for Server |
Allow inbound connections on port 21 |
Allow inbound connections on port 21 and/or 990, 989 |
Allow inbound connections on port 22 |
|
Firewall Port for Client |
Allow outbound connections to port 21 and passive port range defined by server |
Allow outbound connections to port 21 and passive port range defined by server |
Allow outbound connections to port 22 |








