If you think that your WinForms .NET application is from the beginning secure and the source code can't be read, then let me tell you that you're wrong. Anyone can use decompiler that takes an executable file as input, and attempts to create a high level source file (source code of the application). It's recommendable before publishing your application, to check for security flaws on your code by decompiling the generated executable using some decompiling tool. Besides of checking for possible security flaws, if you have inherited an application without documentation or comments, to see how is the behaviour of the compile code with a decompiler could be pretty useful.
If you're willing to decompile assemblies of .NET for any reason, we recommend you for it, to use the ILSpy project. ILSpy is a decompiler and works in the same way Jadx (the APK decompiler) does, however instead of decompiling Java, it decompiles C#. ILSpy is the open-source .NET assembly browser and decompiler. The most know features of this decompiler are:
- Assembly browsing
- IL Disassembly
- Support C# 5.0 “async”
- Decompilation to C#
- Supports lambdas and ‘yield return’
- Shows XML documentation
- Decompilation to VB
- Saving of resources
- Save decompiled assembly as .csproj
- Search for types/methods/properties (substring)
- Hyperlink-based type/method/property navigation
- Base/Derived types navigation
- Navigation history
- BAML to XAML decompiler
- Save Assembly as C# Project
- Find usage of field/method
- Extensible via plugins (MEF)
- Assembly Lists
In this article you will learn how easy is to download ILSpy on your computer and to decompile an executable generated by Visual Studio to finally see its source code.
1. Download ILSpy binaries
There isn't an official installer, ILSpy is portable. The binaries of the ILSpy can be obtained through the releases of the project in Github on the Releases area or just by clicking the Download binaries button from the official website here. The zip contains till the date 11 files (1 executable, 9 dynamic link libraries and a config file):
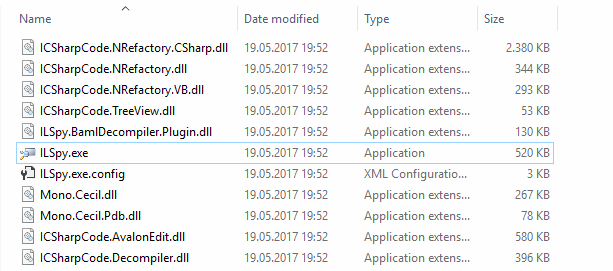
Once downloaded, you can use ILSpy through the executable, it isn't a command line tool as it includes a GUI.
2. Decompiling executables from a WinForms application
Do don't mess with ethic, we are going to decompile one of our own self made applications made with Visual Studio in C#. In our example project we'll expose in the most insecure way a simple login form for a unique user:
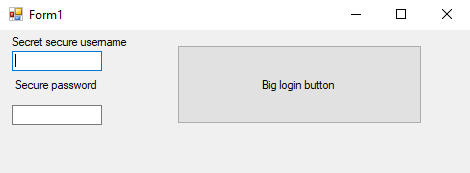
The credentials model is stored in variables in the source code, which is obviously a security flaw. Through an if statement we'll check if the user knows the credentials when the user clicks the login button. The source code of our application is the following:
using System;
using System.Collections.Generic;
using System.ComponentModel;
using System.Data;
using System.Drawing;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
using System.Windows.Forms;
namespace Sandbox
{
public partial class Form1 : Form
{
public string globalUsername = "Batman";
public string globalPassword = "batmobil";
public Form1()
{
InitializeComponent();
}
private void Form1_Load(object sender, EventArgs e)
{
}
private void button1_Click(object sender, EventArgs e)
{
string username = textBox1.Text;
string password = textBox2.Text;
if(username == globalUsername && password == globalPassword)
{
MessageBox.Show("Login granted, awesome !");
}
else
{
MessageBox.Show("Login denied, check your credentials !");
}
}
}
}
Now we'll compile (Build the solution) our project in order to generate the binaries of it in the bin/Debug folder of the project:
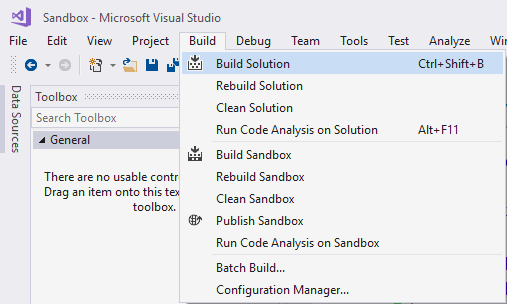
The build solution project will update the debug binaries and you can find the executable of your application in the bin/Debug folder e.g C:\Users\me\Documents\visual studio 2017\Projects\<project-name>\bin\Debug . Open ILSpy, click on File in the Menu Strip and select Open. The filebrowser will start and will allow you to select an assembly, that in this example will be located in the Debug folder of our project:
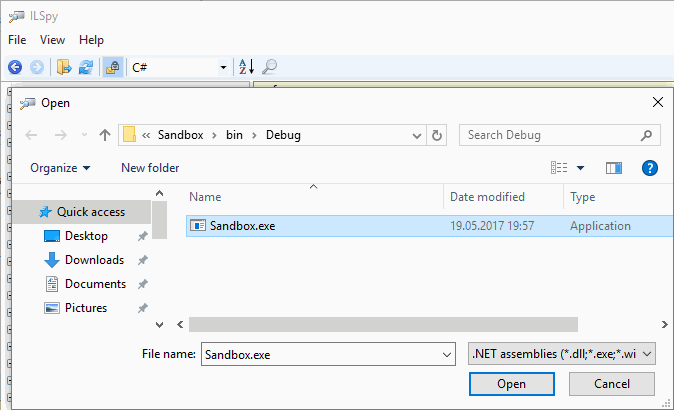
Once you select the executable, ILSpy will start the decompilation process and will add the selected file as an item on the Tree View. There you will be able to explore the structure and resources of the file and the source code. In our example we have a single Form namely Form1 that can be viewed through ILSpy easily:

Do you see it right? ILSpy was able to obtain the source code of our initial application and we can see "the awesome login" algorithm of our WinForms project. The decompilation works obviously with non-debug releases too.
Happy decompiling !








