Although most of the developers publish new projects publicly (the product, an app, whatever), sometimes they want to keep its source code for themselves (closed-source) and that's totally fine. The problem comes when someone that has access to the product, tries to decompile it to obtain some/all of the code that gives life to the product, to find sensitive information that was irresponsibly stored in a string variable on the project (duh). This is a constant problem in the enterprise environment and therefore, there are plenty of possible solutions just as paid products that promise you to protect your executables. If you are looking for an open-source solution for this problem, you landed in the right place.
What's the issue with decompilers
As we wrote in a previous article on how to decompile an executable built with C# using ILSpy, we will do the same in this article to understand what's going on here.
Build an example application
In case you don't have an executable built with C# to test the tool, you need to create one. In our case, we will use a very basic application of a button that launches an alert when it's clicked. The code of this app is the following one in case you need one to test:
using System;
using System.Windows.Forms;
namespace Sandbox
{
public partial class Form1 : Form
{
public Form1()
{
InitializeComponent();
}
private void button1_Click(object sender, EventArgs e)
{
MessageBox.Show(
"Hello There",
"Salutations",
MessageBoxButtons.OK,
MessageBoxIcon.Information
);
}
}
}Build the project and generate an executable. We can use the debug binary (C:\Users\username\source\repos\ProjectName\bin\Debug\Project.exe). Now that you have an executable to test, you can proceed with the rest of the tutorial.
Decompile using ILSpy
If we use the ILSpy utility to decompile the executable build when running the project, you will find the source code of your project (check the button1_Click event):
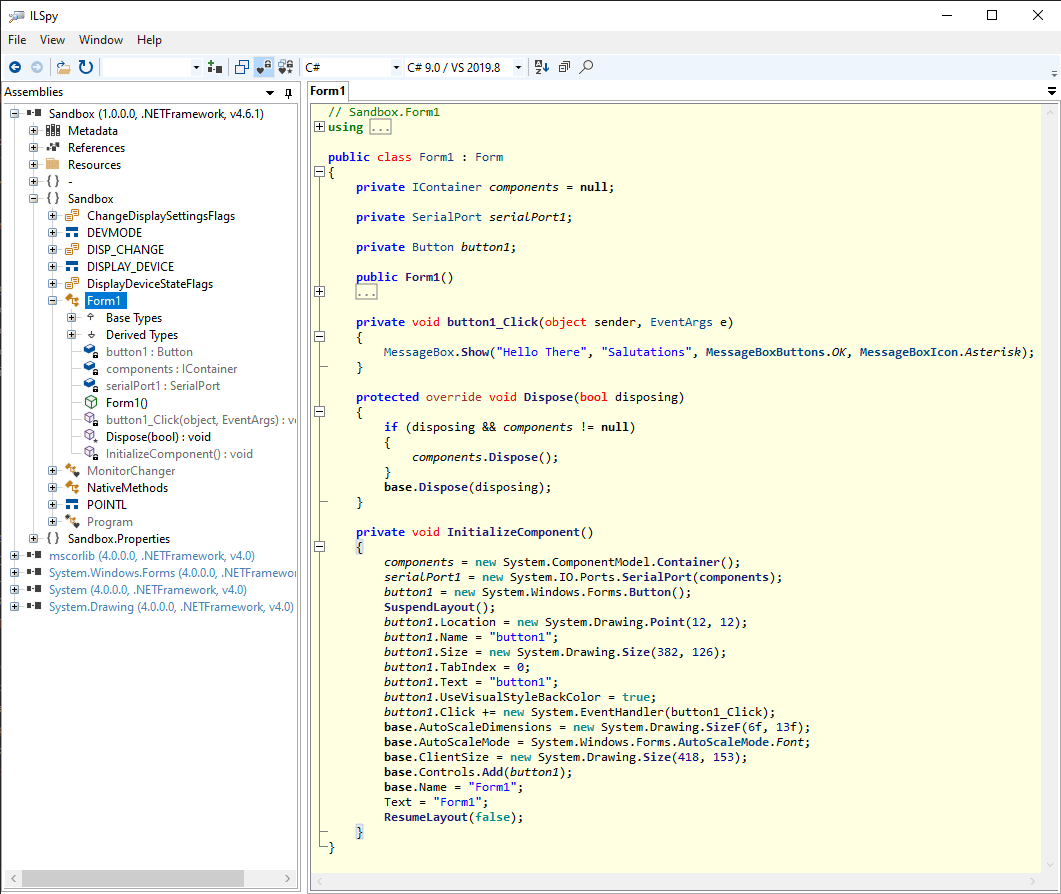
It's very probable that you will recognize some of the code we wrote originally on the project in the decompiled files that ILSpy generated. That's exactly what we are going to prevent from happening in this tutorial.
Protecting your binaries from decompilation
In order to protect the generated binaries of C# project created with .NET, we will use the ConfuserEx tool. ConfuserEx is a open-source protector for .NET applications. It is the successor of Confuser project. However, the ConfuserEx project was officially unmaintained as well and now there's a fork that is being maintained. This project features:
- Supports .NET Framework 2.0/3.0/3.5/4.0/4.5/4.6/4.7
- Symbol renaming (Support WPF/BAML)
- Protection against debuggers/profilers
- Protection against memory dumping
- Protection against tampering (method encryption)
- Control flow obfuscation
- Constant/resources encryption
- Reference hiding proxies
- Disable decompilers
- Embedding dependency
- Compressing output
- Extensible plugin API
- Many more are coming!
Basically what we are going to do is protecting the source code through obfuscation (that's right, an obfuscator of C# just like this obfuscator of JavaScript).
For more information about ConfuserEx, please visit the official repository at Github here.
1. Download ConfuserEx
As the first step, you need to download the latest available release of ConfuserEx. You can find the releases of the project on this page. Be sure to download the version with a Graphical User Interface as that's the one we'll explain in this tutorial. Run the ConfuserEx.exe and continue with the tutorial.
2. Obfuscating executable
Now you need a .NET executable, as we mentioned, you can create a new project with the provided code at the beginning of the article to test or you can immediately proceed with your own project executable. After launching ConfuserEx, you can simply drag and drop the binary that you want to protect or click on the plus symbol at the right side of the application and select your .exe:
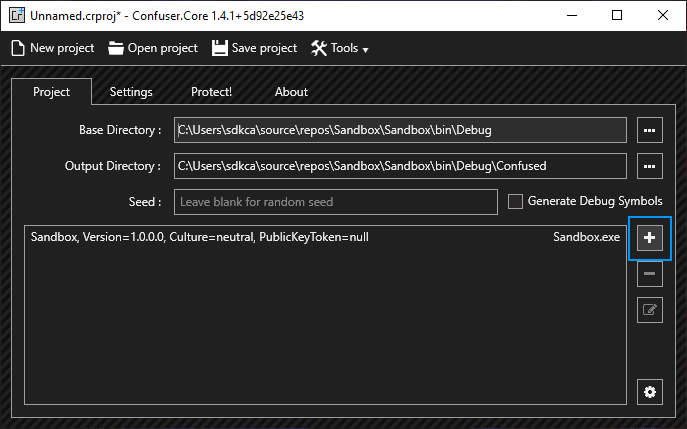
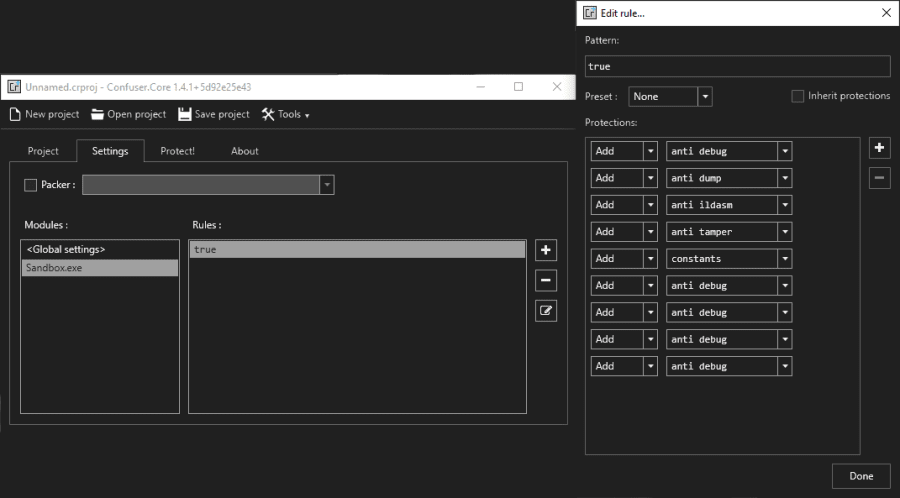
In our case, we will use the Sandbox.exe binary from the debug directory of the project. It's likely that you'll use the production version of the binary, this is just an example. After selecting the file, it will be listed on the project tab. Now you need to go to the Settings tab, you will find in there another list of modules (your executables), where you can apply new rules of protection either globally or to a specific binary. In our case, we will apply the rules of protection globally to any binary we may include in ConfuserEx.
Select the module, then click on the plus icon on the right side of the application. This will add the new rules item that will appear as a single true item. Then, select the true item and click on the edit button on the right side of the application:

Then, a new dialog will appear. In this dialog, you will be able to add rules of obfuscation. You can add a new rule by clicking on the plus icon on the right side of the dialog, for every new item in the protections area you can select the rule name that you want to apply, in our example we will apply every possible item:
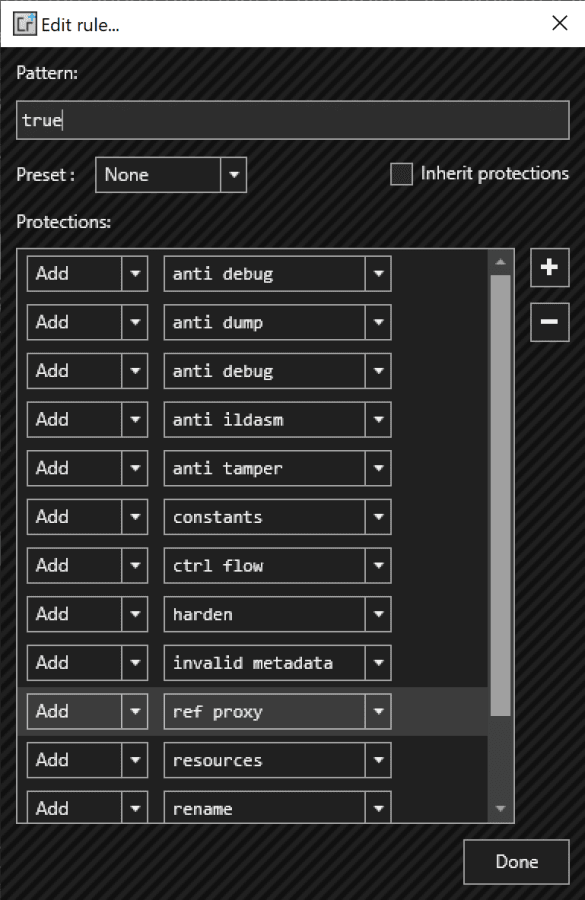
Click on Done and that's it. Finally, go to the settings tab and click on protect:
You will find the new executable that has the protection in the /Confused directory (Output Directory parameter that you can find in the Project tab). The output binary is protected now, so you can try to run ILSpy or any other decompiler on it and you will find that the extracted information is obfuscated.
Happy coding ❤️!