Although a lot of people didn't think they would come back again, desktop applications are getting popular again. In the last years, developers started moving to web applications, however we are living the inverse situation. In the same way hybrid mobile applications with the Cordova Framework got popular, in their desktop counterpart we have the Github's project Electron, a framework to build cross-platform desktop apps with JavaScript, HTML, and CSS. In this trend, Github's Electron has become a popular framework to While it seems to be easy, embedding a web application in a self-contained web environment (Chromium, Node.Js) leads to new security challenges.
In this short article, we would like to introduce you to the electronegativity tool for Electron Framework applications.
What is electronegativity
Electronegativity is a tool to identify misconfigurations and security anti-patterns in Electron-based applications. It leverages AST and DOM parsing to look for security-relevant configurations, as described in the "Electron Security Checklist - A Guide for Developers and Auditors" whitepaper.
Software developers and security auditors can use this tool to detect and mitigate potential weaknesses and implementation bugs when developing applications using Electron. A good understanding of Electron (in)security is still required when using Electronegativity, as some of the potential issues detected by the tool require manual investigation.
During the research of the research of the author of Electron Security Checklist by @lucacarettoni, the developers of the tool extensively studied the security of the Electron framework itself and reported vulnerabilities to the core team. However, they focus on the application-level design and implementation flaws only.
How to use it
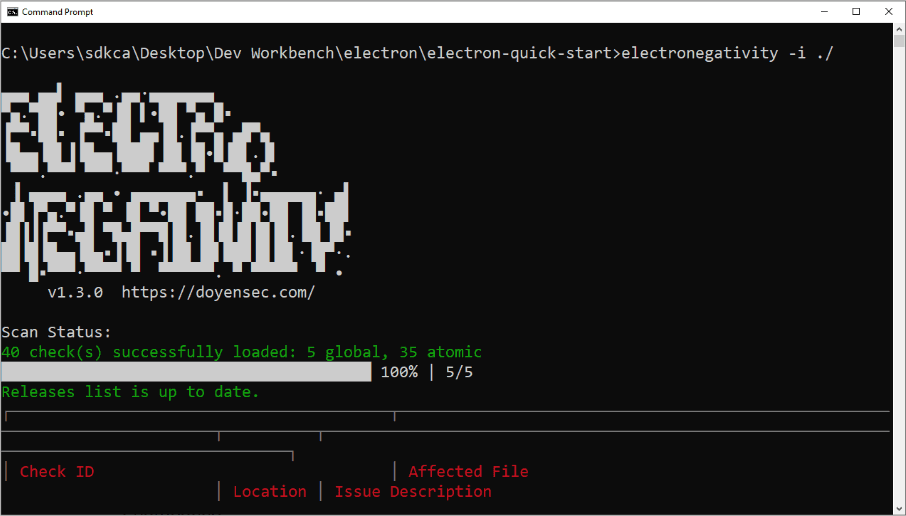
To install this package on your system, run the following command on your terminal:
npm install @doyensec/electronegativity -gThis will install the electronegativity package globally on your system. After the installation, you can easily look for issues in a directory containing an Electron app:
electronegativity -i ./project-directoryThe command electronegativity supports the following options:
| Option | Description |
|---|---|
| -V | output the version number |
| -i, --input | input (directory, .js, .html, .asar) |
| -l, --checks | only run the specified checks, passed in csv format |
| -s, --severity | only return findings with the specified level of severity or above |
| -c, --confidence | only return findings with the specified level of confidence or above |
| -o, --output <filename[.csv or .sarif]> | save the results to a file in csv or sarif format |
| -r, --relative | show relative path for files |
| -h, --help | output usage information |
For example if you want to generate a CSV with the information of the report:
electronegativity -i ./project-directory -o report.csvThe following command will generate a CSV report with the following information:
| issue | severity | confidence | filename | location | sample | description | url |
|---|---|---|---|---|---|---|---|
| AUXCLICK_JS_CHECK | MEDIUM | FIRM | C:\Users\sdkca\Desktop\Dev Workbench\electron\electron-quick-start\main.js | 11:15 | mainWindow = new BrowserWindow({ | Limit navigation flows to untrusted origins. Middle-click may cause Electron to open a link within a new window | https://github.com/doyensec/electronegativity/wiki/AUXCLICK_JS_CHECK |
| CONTEXT_ISOLATION_JS_CHECK | HIGH | FIRM | C:\Users\sdkca\Desktop\Dev Workbench\electron\electron-quick-start\main.js | 11:15 | mainWindow = new BrowserWindow({ | Review the use of the contextIsolation option | https://github.com/doyensec/electronegativity/wiki/CONTEXT_ISOLATION_JS_CHECK |
| NODE_INTEGRATION_JS_CHECK | INFORMATIONAL | FIRM | C:\Users\sdkca\Desktop\Dev Workbench\electron\electron-quick-start\main.js | 15:6 | nodeIntegration: true | Disable nodeIntegration for untrusted origins | https://github.com/doyensec/electronegativity/wiki/NODE_INTEGRATION_JS_CHECK |
| SANDBOX_JS_CHECK | MEDIUM | FIRM | C:\Users\sdkca\Desktop\Dev Workbench\electron\electron-quick-start\main.js | 11:15 | mainWindow = new BrowserWindow({ | Use sandbox for untrusted origins | https://github.com/doyensec/electronegativity/wiki/SANDBOX_JS_CHECK |
| CSP_GLOBAL_CHECK | MEDIUM | CERTAIN | N/A | 0:0 | N/A | No CSP has been detected in the target application | https://github.com/doyensec/electronegativity/wiki/CSP_GLOBAL_CHECK |
| LIMIT_NAVIGATION_GLOBAL_CHECK | HIGH | CERTAIN | N/A | 0:0 | N/A | Missing navigation limits using .on new-window and will-navigate events | https://github.com/doyensec/electronegativity/wiki/LIMIT_NAVIGATION_GLOBAL_CHECK |
| PERMISSION_REQUEST_HANDLER_GLOBAL_CHECK | MEDIUM | CERTAIN | N/A | 0:0 | N/A | Missing PermissionRequestHandler to limit specific permissions (e.g. openExternal) in response to events from particular origins. | https://github.com/doyensec/electronegativity/wiki/PERMISSION_REQUEST_HANDLER_GLOBAL_CHECK |
For more information about this tool, please visit the official repository at Github here and don't forget to read the BlackHat 2017 research Electronegativity - A Study of Electron Security and keep an eye on the Doyensec's blog.