When you download a file from the internet on a Windows computer, it often comes with something hidden attached, a mysterious piece of metadata known as the Zone.Identifier. You won't see it listed in File Explorer, but it quietly influences how Windows treats that file. From triggering "This file came from another computer" warnings to blocking scripts and executables, the Zone.Identifier plays a crucial role in Windows’ security model. In this article, we'll explore what the Zone.Identifier actually is, why Windows creates it, and how to remove it safely without compromising your system's protection.
What are Zone.Identifier Files
A Zone.Identifier file is a hidden metadata file, technically called an Alternate Data Stream (ADS) that Windows automatically attaches to files downloaded from the internet or received from external sources such as email attachments or network drives. This data stream is used by Windows to mark the origin or security zone of the file, indicating where it came from.
The Origin of Zone.Identifier Files
The Zone.Identifier file, often seen as an alternate data stream (ADS) attached to downloaded files on Windows, was introduced with Windows XP Service Pack 2 and Windows Server 2003 Service Pack 1. These updates added a new security mechanism known as Mark of the Web (MOTW), a system designed to protect users from running potentially unsafe files obtained from the Internet. When a file is downloaded using Internet Explorer or another compliant application, Windows automatically appends an ADS named Zone.Identifier. This hidden stream contains metadata about the file’s origin, such as its security zone:
-
ZoneId=3: Assigned to files from the Internet
-
ZoneId=2: Assigned to Trusted sites
-
ZoneId=1: Assigned to file from Intranet
-
ZoneId=0: A file from the Local machine
When a user later attempts to open such a file, Windows (and apps like Microsoft Office or PowerShell) can check the Zone.Identifier data and warn the user if the file came from an untrusted source. The introduction of Zone.Identifier files marked a significant shift toward content-origin awareness in Windows security. Before the MOTW, downloaded files were treated no differently from local files, creating easy openings for malware. Today, many tools such as email clients and antivirus software rely on these hidden tags to make security decisions.
They're invisible in normal Windows Explorer
By default, Windows File Explorer and most applications do not show Zone.Identifier files, because they aren't actually separate files. Instead, they are Alternate Data Streams (ADS), a special NTFS feature that allows multiple data streams to be attached to a single file.
So, for example, if you download a file called file.pdf, the actual data on disk looks like this:
- file.pdf
- file.pdf:Zone.Identifier
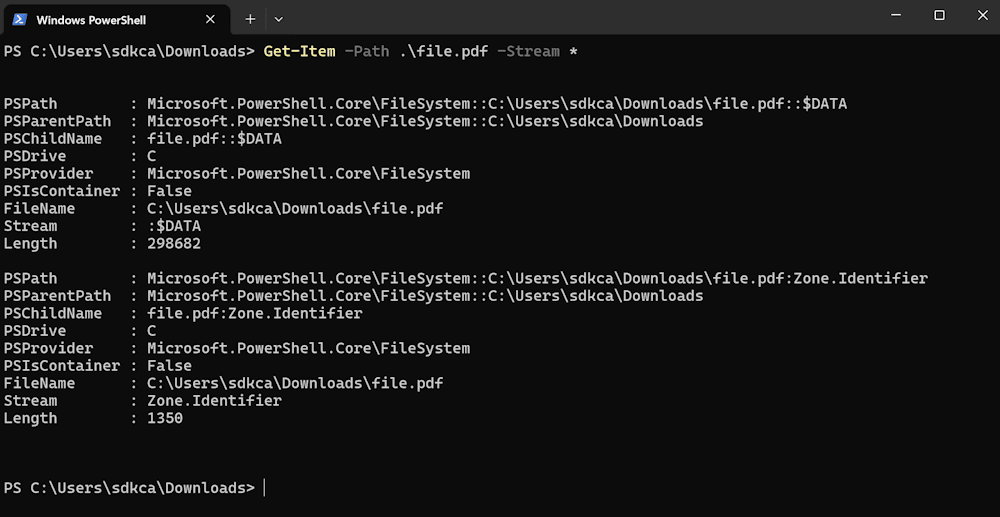
So it's possible to see them in Windows for example using Powershell with the following command:
Get-Item -Path .\file.pdf -Stream *The output should look similar to:
What Are Alternate Data Streams (ADS)?
Alternate Data Streams (ADS) are a feature of the NTFS file system that allows a single file to contain multiple streams of data, not just the main file content you see, but also additional "hidden" streams of information. Every file on an NTFS volume has at least one stream. ADS was originally introduced to support compatibility with Apple's Hierarchical File System (HFS), which used resource forks, a similar concept. When Microsoft added NTFS in the early 1990s, it needed a way to preserve that kind of extra metadata, so Alternate Data Streams were born.
Are There Alternate Data Streams in Linux?
While Windows NTFS supports Alternate Data Streams (ADS) — hidden data channels attached to a single file — Linux takes a different approach. There's no counterpart to ADS, but Linux filesystems do offer mechanisms that serve similar purposes for storing additional file information. The closest equivalent to ADS in Linux is the concept of Extended Attributes, often abbreviated as xattr. These attributes allow users and applications to attach extra metadata to files, without changing the file’s visible contents.
Each attribute is stored as a key–value pair, for example:
user.comment = "Reviewed by Carlos"
security.selinux = "system_u:object_r:user_home_t:s0"Security risks of Zone.Identifier (NTFS Alternate Data Streams)
While this metadata supports helpful features like SmartScreen warnings, it also creates several security risks that attackers can exploit. Zone.Identifier is a hidden trust signal. Because many tools and policies use its presence (or absence) to decide whether a file is "safe" attackers who can remove, spoof, or hide that ADS can bypass warnings, hide payloads, or leak information. Relying on it as a single source of truth creates dangerous blind spots.
Main risks
1. Bypassing platform defenses
-
Stripped metadata = fewer warnings. If an attacker or a delivery mechanism removes the
Zone.Identifierstream (for example, by copying via a non-NTFS volume, packaging into some ZIP utilities, or explicitly deleting the ADS), Windows may treat the file as local and avoid SmartScreen/Mark-of-the-Web prompts. -
Automated systems fooled. Deployment or endpoint controls that trust files lacking an Internet zone marker can inadvertently execute malware.
2. Information disclosure
-
Zone.Identifiercan containReferrerUrlandHostUrl. When shared or exfiltrated, these values can reveal:-
internal URLs or network topology,
-
which internal systems served downloads,
-
browsing/referrer patterns that help an attacker profile a target environment.
-
3. Concealment & persistence via alternate streams
-
NTFS ADS allow data to be hidden inside a file without changing the visible filename (e.g.,
document.pdf:payload.exe). Malware can hide components or configuration data in ADS to avoid casual inspection and some signature-based scanners. -
ADS-based payloads can persist and be overlooked during routine file listing or user inspection.
4. Privilege-elevation and evasion
-
Attackers can use ADS to hide scripts or signed binaries and then execute them via less-scrutinized paths. This can help malware escalate privileges or evade detection by security tools that don’t scan alternate streams.
5. Misplaced trust and automation weaknesses
-
Relying on
Zone.Identifieras a binary “safe/unsafe” flag is fragile. Attackers can spoof zone values or remove the ADS during transfer, while defenders using this heuristics produce false negatives (malicious files that appear safe).
Real-world attack patterns
-
Delivery chain manipulation: An attacker distributes a malicious executable inside a ZIP created on a FAT-formatted USB or uploaded through a service that strips ADS — the resulting executable is missing the zone marker and bypasses SmartScreen on the target machine.
-
ADS payload hiding: A benign-looking document contains an ADS with an embedded executable; a script extracts and runs the ADS payload later.
-
Automated deployment trick: A CI/CD pipeline that whitelists “internal” binaries based on absence of a ZoneId will accept a malicious binary whose ADS was removed earlier in the chain.
Zone.Identifier Files in WSL
When using the Windows Subsystem for Linux (WSL), you might notice that files downloaded from the internet sometimes appear with an extra file beside them, something like example.txt:Zone.Identifier. This happens because WSL recognizes Windows Alternate Data Streams (ADS), such as the Zone.Identifier, as separate visible files instead of hidden metadata. We wrote previously an article about how to delete Zone.Identifier files from WSL in case you're interested in deleting them.
How to Delete Hidden Data Streams
Alternate Data Streams (ADS) and Extended Attributes can be useful for metadata and security purposes — but sometimes you may want to remove them to protect privacy, clean up files, or prevent false security warnings. The most efficient way to delete the hidden Zone.Identifier stream in Windows is through PowerShell, which provides direct access to a file’s alternate data streams (ADS). Each downloaded file on an NTFS drive may include a secondary stream named Zone.Identifier that stores its origin information. To remove it, simply run the command:
Remove-Item -Path "C:\Path\to\file.ext" -Stream Zone.IdentifierAfter running these commands, the file will no longer carry the "This file came from another computer" warning, making it behave like a locally created file. This method is quick, safe, and doesn't require third-party tools, ideal for cleaning large sets of downloaded documents or scripts.
Final Thoughts
Hidden metadata like Zone.Identifier files and Alternate Data Streams may seem obscure, but they play an important role in how modern operating systems handle security and trust. Understanding how these data streams work, how to inspect them, and how to remove them using tools like PowerShell gives you full control over what’s stored in your files. Meanwhile, Linux’s extended attributes (xattr) offer a more structured, transparent approach to metadata, showing how each system solves the same problem in its own way.
Whether you're a developer, digital forensics analyst or a privacy-conscious user, knowing how to manage these invisible pieces of data ensures your files are not only cleaner but also safer.









